The Future of Business: Embracing Cloud Computing

You may have noticed a significant shift in how businesses operate, largely driven by the rise of cloud computing. This technology has transformed the landscape of data storage and management, allowing organizations to access and utilize resources over the internet, rather than relying on local servers or personal computers. The concept of cloud computing emerged […]
Leveraging Data Quality: Survey Design Tips
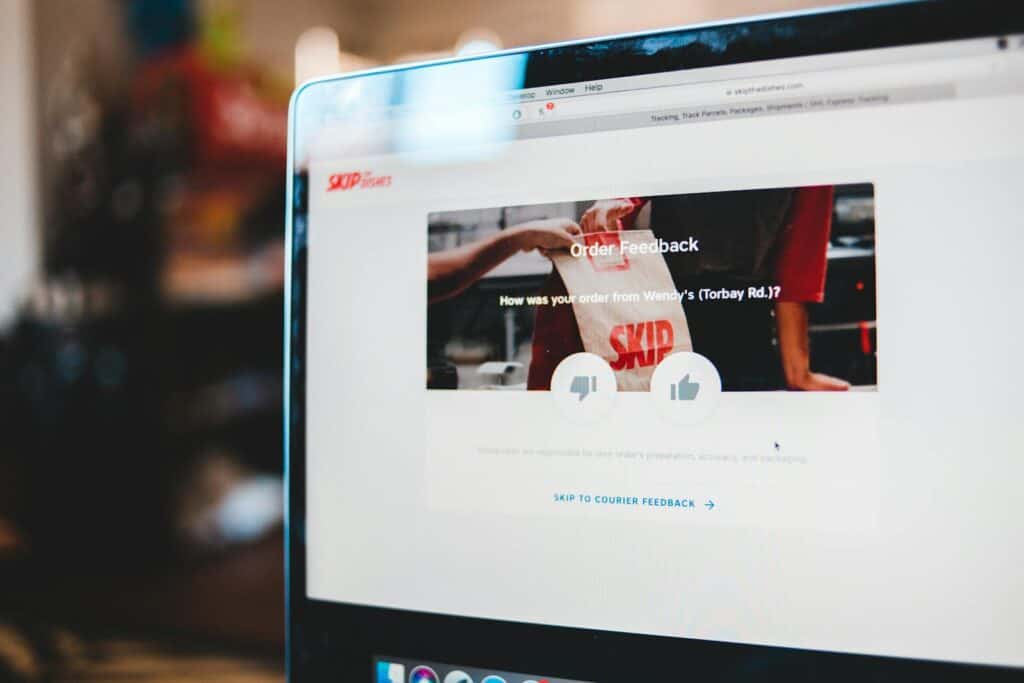
The quality of the information you collect can significantly impact your decision-making processes. Data quality refers to the accuracy, completeness, reliability, and relevance of the data you gather. When you conduct a survey or research project, understanding the nuances of data quality becomes paramount. High-quality data enhances the credibility of your findings and ensures that […]
Harnessing the Power of Polls for Marketing Impact

Polls serve as a useful tool for gathering insights and understanding consumer preferences. They provide a snapshot of public opinion and help you gauge the effectiveness of your marketing strategies. By engaging your audience through polls, you can tap into their thoughts and feelings, allowing you to tailor your campaigns to better meet their needs. […]
Securing Data: The Importance of Encryption

Encryption is a fundamental concept in data security, and understanding it is crucial for anyone who interacts with digital information. At its core, encryption is the process of converting plain text into a coded format, known as ciphertext, which can only be read by someone who possesses the correct decryption key. This transformation ensures that […]
Boosting Facebook Engagement: Tips and Tricks for Success

To effectively utilize the world of Facebook marketing, it is crucial for you to grasp the intricacies of the platform’s algorithm. The Facebook algorithm determines what content appears in users’ news feeds, influencing the visibility of your posts. It prioritizes content based on various factors, including user engagement, relevance, and recency. By understanding how this […]
Cracking the Instagram Algorithm for Success

The Instagram algorithm is designed to curate content that appears in users’ feeds, based on their interests and interactions. This means that the more you engage with certain types of content, the more likely you are to see similar posts in the future. Understanding this mechanism can significantly enhance your visibility and engagement on the […]
Leveraging LinkedIn for Lead Generation

LinkedIn has become a potent tool for professionals looking to network, connect and create leads. Being able to use this platform efficiently can greatly increase your business prospects. In order to make the most of your potential on this professional network, this article will walk you through the key tactics for using LinkedIn for lead […]
Secure Your Website with WordPress Hosting Security

When you create a WordPress website, one of the most critical aspects to consider is security. The digital space is fraught with potential threats, and your website can become a target for hackers and malicious entities. Understanding the importance of WordPress hosting security is not just about protecting your site; it’s about safeguarding your reputation, […]
Crafting the Perfect Logo: A Guide to Effective Design with a logo of a sleek, modern icon.
A strong logo is the foundation of your brand’s identity. Since it frequently serves as the initial impression that prospective clients will have of your company, it is imperative that you communicate the correct message right away. A logo is a single visual representation of your company’s values, mission, and personality. If done well, it […]
Protecting Your Data: Essential Breach Prevention

A data breach occurs when unauthorized individuals gain access to sensitive information, which can include personal identification details, financial records, or proprietary business data. You may find yourself wondering how these breaches happen. Often, they result from cyberattacks, such as phishing schemes or malware infections, but they can also occur due to human error or […]
